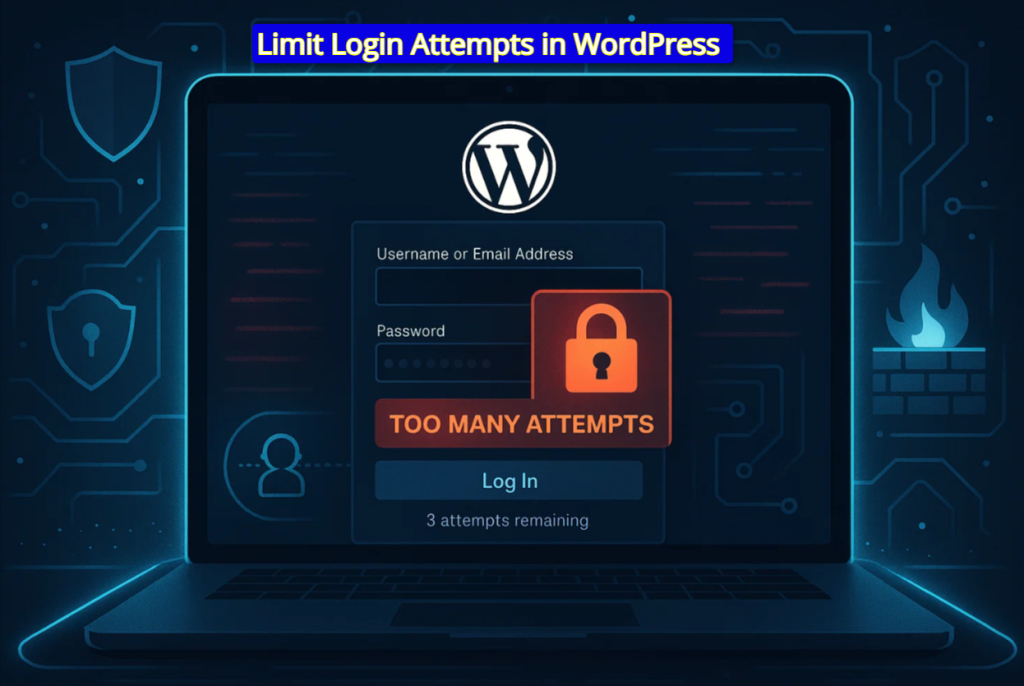
While running a WordPress site, you might think, “Who’d bother hacking my site?” You will realize the truth after seeing hundreds of failed login attempts on your site with a proper tool. WordPress allows unlimited login attempts, which makes it an open target for brute-force attacks.
The attacks usually occur through the WordPress administrator login or any other WordPress login form. Thus, learning how to limit login attempts in WordPress has become a mandatory step to secure your site.
This article will show you why limiting login attempts matters and how you can easily implement it. Plus, you’ll learn additional measures to lock out the bots and prevent malicious login attempts WordPress-wide.
Table of Contents
Why Default WordPress Settings are Not Enough
According to a 2025 security report, attacks per domain increased by 120% in the past year. Besides, Security providers blocked over 55 billion password attacks in 2024 alone across the WordPress ecosystem.
Because WordPress powers a large share of the web, attackers see value in trying to break into even simple sites. A bot could try thousands of username-password combinations in minutes and ultimately breach your site.
When someone tries to log into WordPress, the server checks the submitted credentials. If they fail, the user can try again immediately. A human might give up after five or ten tries, but a malicious bot doesn’t.
The Mechanism of a Brute Force Attack
Brute force attacks are pure trial-and-error. They exploit the open-door policy of the standard WordPress login screen:
- Bot Network: Attackers use large networks of compromised computers (botnets) to launch an attack across many IPs. This makes it hard to block a single source of attack.
- Dictionary Attacks: The bots use vast databases of common usernames (like ‘admin’) and weak passwords, or credentials stolen from other data breaches (known as credential stuffing).
- Relentless Guessing: These scripts can execute hundreds or even thousands of login attempts per minute, putting an enormous strain on your hosting server. They will keep going indefinitely until they successfully log in to WordPress.
The Dual Damage: Security Breach and Performance Hit
A successful breach is the worst possible situation for a site owner. It comes with malware, data theft, SEO poisoning, and complete loss of control. However, even after blocking malicious login attempts, WordPress causes significant problems:
- Server Overload: Each failed login attempt consumes your server’s resources. A sustained attack can slow your site to a crawl. This leads to poor user experience, timeouts, and potential downtime. Overall, your site gets a severe hit to your SEO ranking and brand reputation.
- Search Engine Penalty: If your site becomes infected or inaccessible due to a brute force attack, Google may blacklist your domain. According to various security reports, Google blacklists around 70,000 websites every week due to security issues. A hack can result in a devastating loss of traffic and authority.
This is why the strategically deploying limit login attempts in WordPress mechanism is the single most effective first-line defense for securing your WordPress administrator login.
The Cornerstone Solution: How to Limit Login Attempts in WordPress
The most practical and user-friendly way to implement this essential security feature is by using a dedicated, well-maintained plugin. While code-based solutions exist, they risk breaking your site with an incorrect snippet. Plus, they require ongoing maintenance that most site owners simply don’t have time for.
While Limit Login Attempts Reloaded is the undisputed champion of limit login attempts in WordPress. But is it enough to protect the login page? No, because WordPress administrator login often requires more comprehensive features that typically reside behind a premium paywall.
This is where Admin Safety Guard Pro emerges as an excellent, budget-friendly alternative that bundles “premium” features into its free core offering.
Admin Safety Guard
Admin Safety Guard focuses on hardening the entire admin area and login flow. It allows you to limit login attempts in WordPress with layered protection against malicious login attempts. So, you won’t require multiple plugins to safeguard your site. The plugin shifts the defensive strategy from solely limiting attempts to making the login page itself harder to find and crack.
Here is what you will get when compared to Limit Login Attempts Reloaded in its free version
| Feature Category | Limit Login Attempts Reloaded (Free) | Admin Safety Guard (Free) | Advantage for Admin Safety Guard |
| Login Attempt Limit | ✅ Yes (Core Feature) | ✅ Yes | Equal core brute force protection. |
| Change Login URL | ❌ No | ✅ Yes | Hides the default /wp-admin URL instantly, stopping automated bots. |
| Two-Factor Auth (2FA) | ❌ No | ✅ Yes | Adds a vital second layer of security (often a premium feature elsewhere). |
| CAPTCHA Protection | ❌ No | ✅ Yes | Stops bots before they even hit the attempt limit. |
| Disable XML-RPC | ❌ No | ✅ Yes | Closes a major backdoor used for amplification attacks. |
| IP Blocking/Whitelisting | ✅ Yes (Free) | ✅ Yes | Essential control over access. |
Enabling and Setting Up Limit Login Attempts in WordPress
Here is the detailed step-by-step guide to enable limit login attempts in WordPress using the Admin Safety Guard plugin.
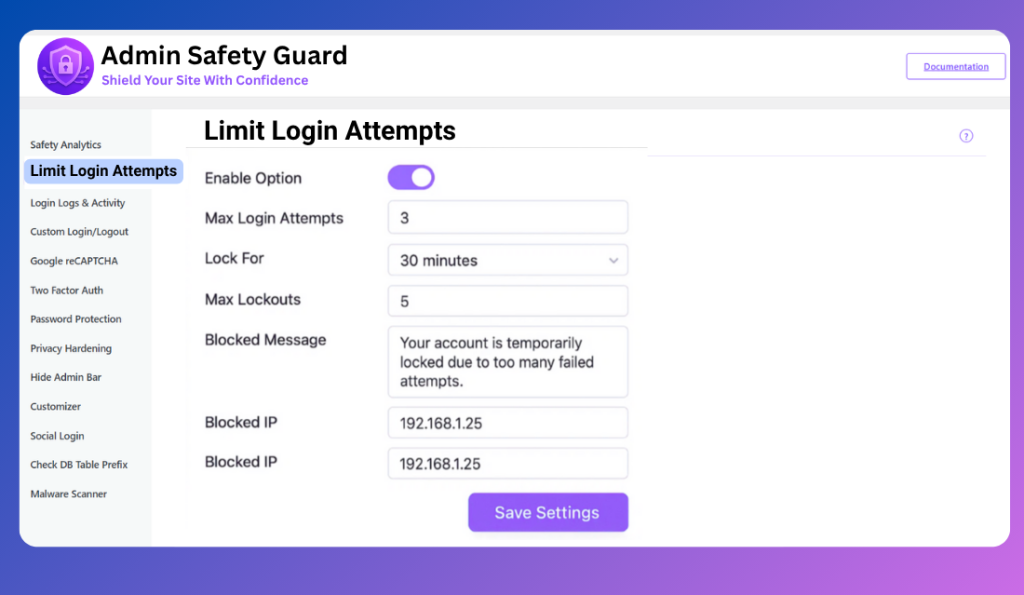
Enable Limit Login Attempts in WordPress Feature
First, you need to activate the primary functionality of the security plugin you’re using.
- Navigate to the security settings area within your WordPress dashboard.
- Locate the Limit Login Attempts feature.
- Enable the feature by tapping the designated button (it might be labeled Enable, Turn On, or Activate).
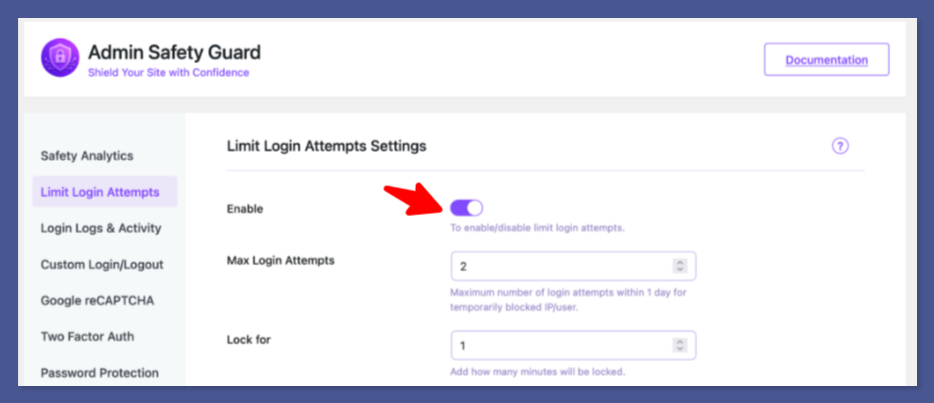
Once enabled, the system is ready to enforce your security rules, which you will set in the following steps.
Define Max Login Attempts (The Initial Limit)
This setting defines the threshold for the first, temporary lockout.
- Find the option labeled “Max Login Attempts” or “Allowed Retries”.
- In the space provided, enter your preferred number. A secure recommendation is 3–5.
- Example: If you enter 3, a user attempting to log in to WordPress will be allowed only three incorrect credential attempts before being temporarily blocked.
- Click Save Settings.
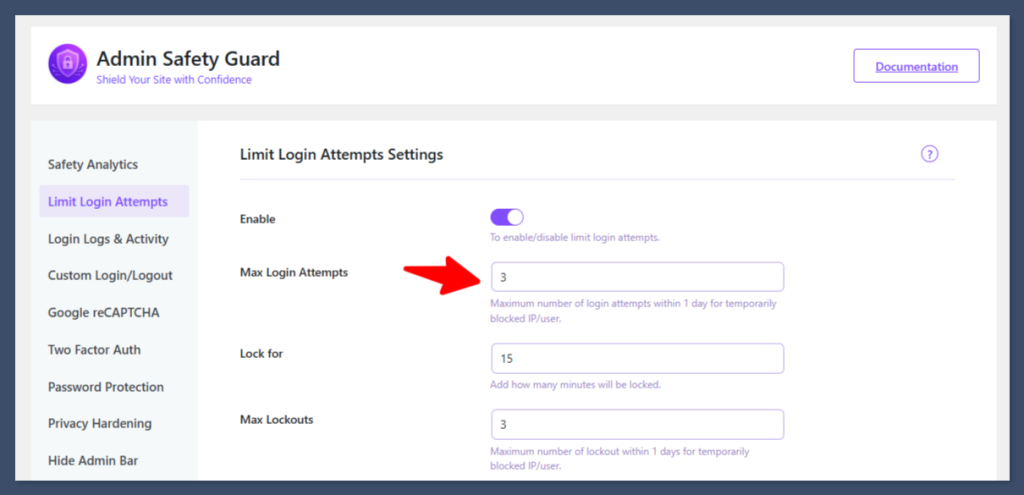
Verification: You can now test this. Navigate to your website’s login area and attempt to log in with incorrect credentials three times. You will be locked out of the website, which brings us to the next step: setting the duration.
Set Lock For (Temporary Lockout Duration)
This specifies how long an IP address is blocked after hitting the Max Login Attempts limit.
- Locate the setting labeled Lock For or Minutes Lockout.
- Specify the duration you want the user to be blocked from accessing your site.
Example: Specify 15 minute (or ideally, 20–60 minutes for stronger security).
- Click Save Settings.
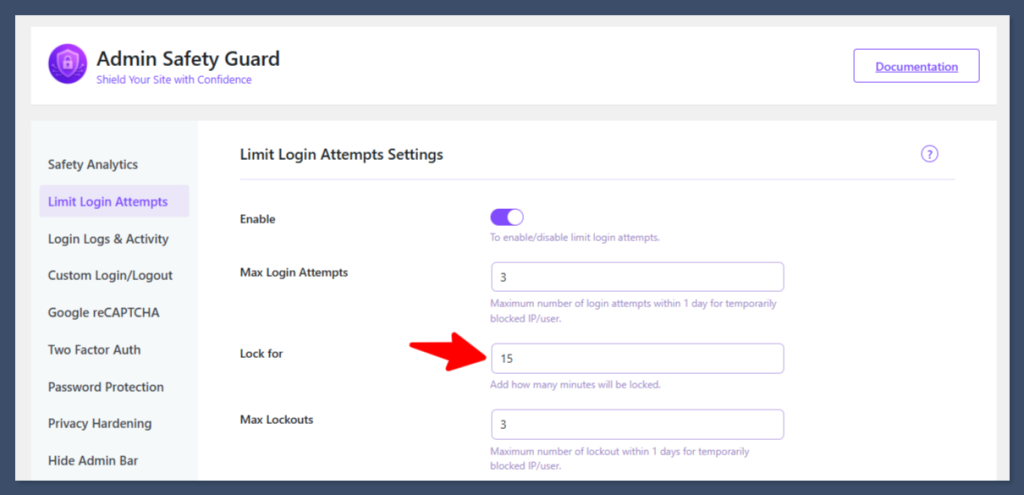
Verification: If you attempt to log in three times (as previously set in Step 2), you will be blocked from the site for the specified duration (e.g., 1 minute). You must wait this time to re-enter the site using the proper credentials.
Configure Max Lockouts (Permanent/Extended Blocking)
This option prevents relentless, sustained attacks by setting a limit on how many temporary lockouts an IP can incur before facing a permanent or very long-term block.
- Find the setting labeled Max Lockouts or Lockouts Increase Lockout Time By.
- Set the number of total lockouts allowed.
Example: If you set this to 3, it means the user can be temporarily blocked three times.
- Click Save Settings.
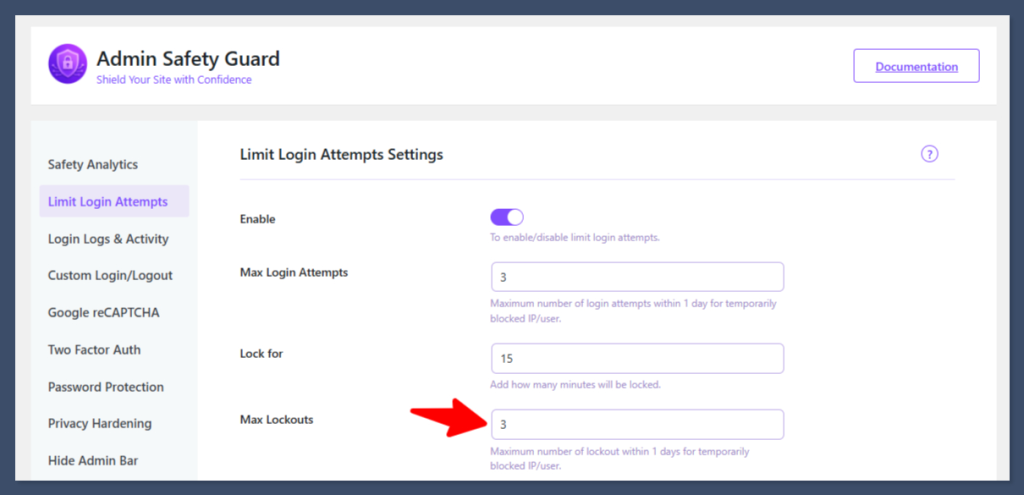
Result: Now, if the same user attempts to log in incorrectly, gets locked out, and repeats this process a total of 2 times, they will trigger the Max Lockouts rule, resulting in a significantly longer block (often 1 day or permanent).
Note: People blocked for a short duration (e.g., 1 minute) are typically not listed in the Login Logs & Activity tab; only those blocked by the Max Lockouts rule will be logged for administrative review.
Create a Block Message
Setting a clear message can inform legitimate users what happened and deter malicious users.
- Locate the option labeled Block Message.
- Insert the custom message you want to display when someone is blocked from your site (e.g., “Access Denied: You have exceeded the maximum login attempts. Please try again in 24 hours.”).
- Click Save Settings.
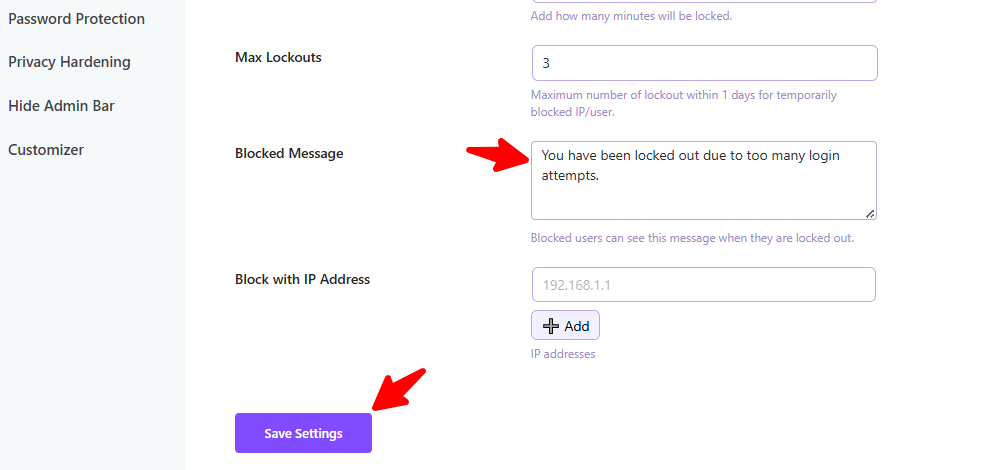
Verification: After two consecutive failed login attempts that lead to a lockout, an attempting user will see this custom blocked message on the login WordPress screen.
Block With IP Address (Manual Blocking)
This feature allows you to manually and instantly block known malicious IP addresses detected from your Login Logs or other security monitoring tools.
- Find the box labeled Block with IP Address.
- Put the specific IP address of a user you wish to block.
- For multiple IP addresses, insert each one, often separated by a comma or on a new line (check the plugin’s specific instructions).
- Click the Save Settings button.
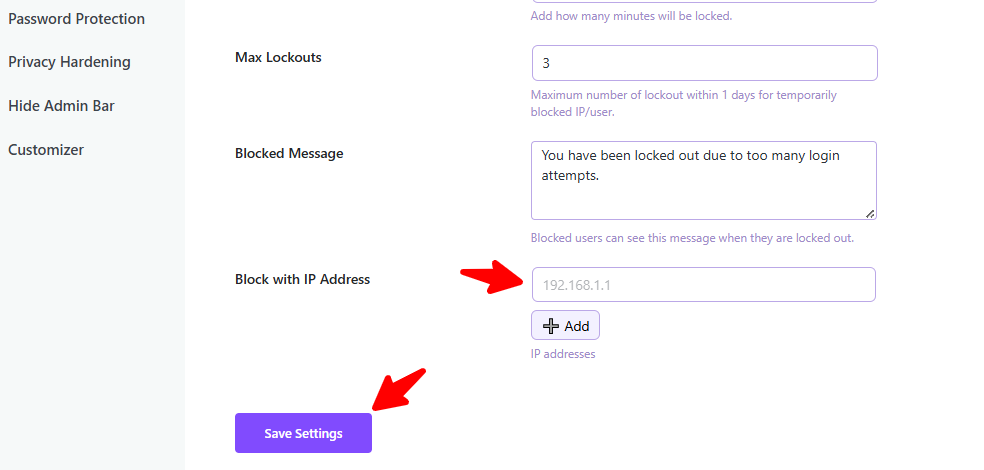
Result: If any user attempts to log in from that blocked IP address, they will be immediately unable to access the site, protecting your WordPress site admin login from known threats.
Benefits for SEO and Site Health With Limit Login Attempts in WordPress
Implementing a defense with limit login attempts in WordPress is not just about security. This feature gives you strategic advantages like site performance and search engine optimization.
Server Load Management and Core Web Vitals
Google considers Core Web Vitals (loading speed, interactivity, and visual stability) as a ranking factor.
- The Connection: A heavy brute force attack, even an unsuccessful one, can generate thousands of requests that consume CPU and RAM. This slows down page loading for legitimate users and can even lead to your server returning a 503 Service Unavailable error.
- The Solution: The limit login attempts in WordPress can drastically reduce the sheer volume of malicious requests, freeing up server resources. This directly translates to faster page load times and better performance metrics. Therefore, you are not just blocking hackers; you are optimizing your server’s health.
Protecting Your Content and Authority
Hacked website brings in SEO disaster for a website. Hackers often inject malicious code that redirects visitors to spam sites, displays phishing content, or cloaks hidden spam links.
- The Impact: Google will detect this, issue a massive security warning to all potential visitors, and swiftly de-index your pages. Recovering your organic traffic and authority from this kind of penalty is a long, painful process.
- The Defense: With limit login attempts in WordPress, you are safeguarding your content. This leads to preserving your domain’s trust signals, and ensuring that all your content writing efforts continue to be rewarded in the SERPs.
Defence strategies Beyond Limit Login Attempts in WordPress
While setting a limit login attempts in WordPress is essential, true security requires a multi-layered defense. Combine rate-limiting with these robust measures:
Two-Factor Authentication (2FA)
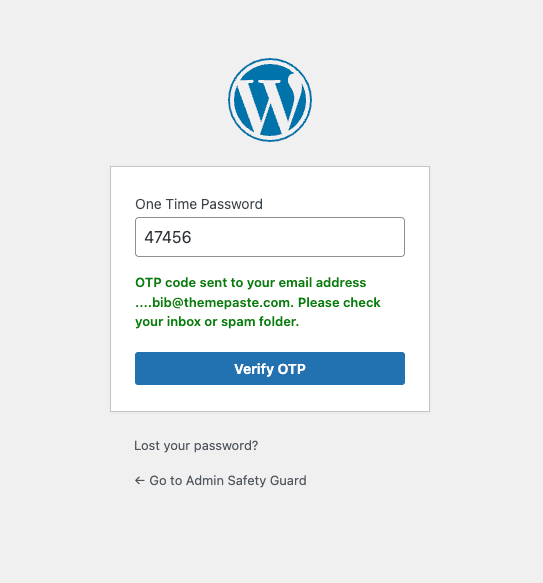
Ultimate Failsafe: If credentials are cracked, Two factor authentication prevents access. After entering the password, the user must provide a second, time-sensitive code from their physical mobile device (via an app like Google Authenticator).
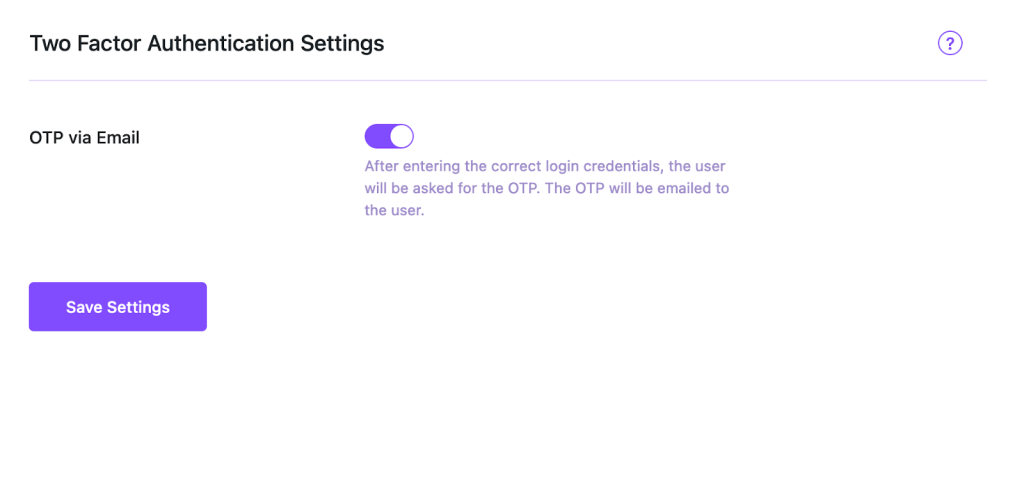
The Power: Even with the correct username and password for your WordPress site admin login, the attacker is locked out. This makes brute force attacks nearly worthless.
Move Your WordPress Login URL
Instant Bot Stopper: Default login paths (/wp-admin, /wp-login.php) are bot targets. Changing this URL stops automated attacks instantly.
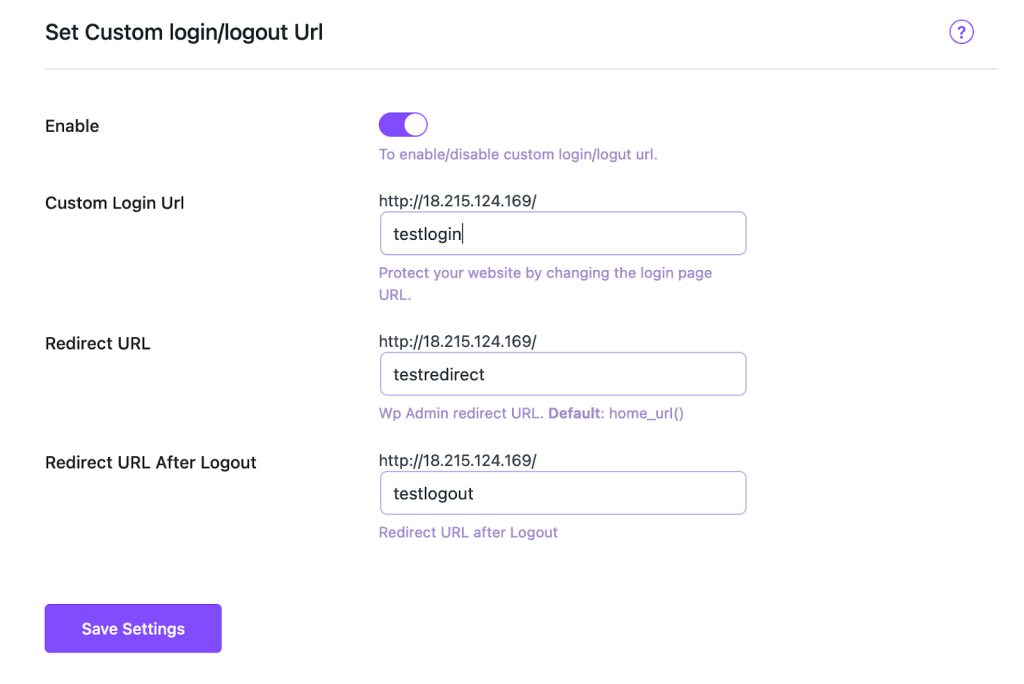
Actionable Step: Use a security plugin to move your default login WordPress URL to a secret, unique address (e.g., /my-secret-admin-page). Bots can no longer find the form, making the majority of blocked malicious login attempts WordPress irrelevant.
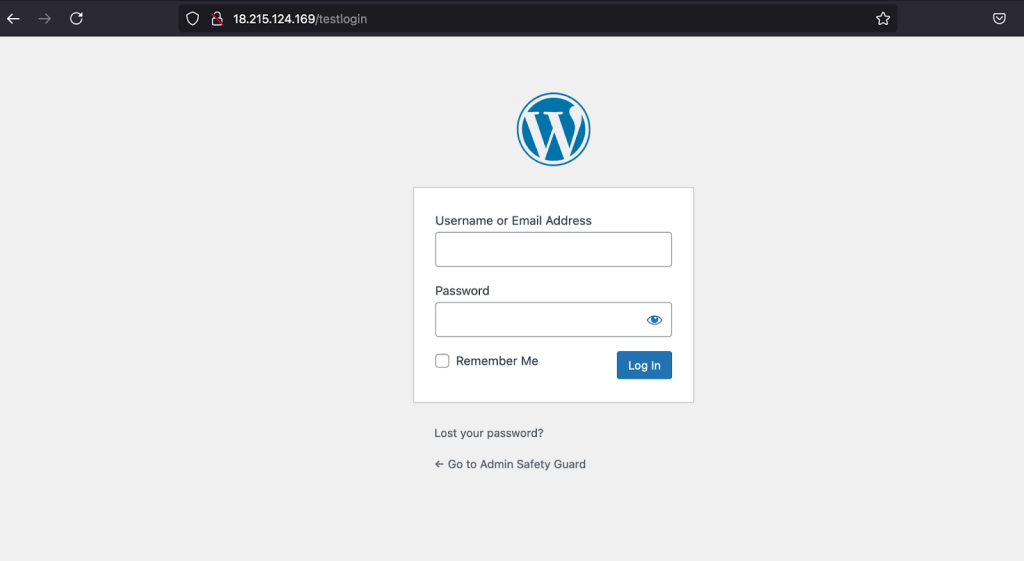
Create an Uncommon Administrator Username
Stop the Guessing Game: Bots primarily target common usernames like admin. Using these makes you highly vulnerable.
Best Practice: Never use ‘admin’. Use a unique, complex username that cannot be guessed. This forces the attacker to guess two unknowns (username and password), drastically reducing the chances of a successful attack.
Final Thoughts: Fortify Your WordPress Site
As a WordPress site owner, you may face constant brute force onslaught. Therefore, you should never ingnore the power of the need to limit login attempts in WordPress.
Moreover, implementing advanced strategies like 2FA, renaming admin URL, and using a WAF makes your site hard target. You are not only blocking attackers but also preserving your site’s authority with these techniques. Take action today to secure your login WordPress page and avoid the pain of a post-hack recovery.